The popularity of the internet has eventually grown, and the businesses have started to extend their own networks. Earlier ‘Intranet’ was introduced and was widely in use as a linking hub accessed only by the company employees, but now companies build their own Virtual Private Network (VPN) to communicate with their branch-offices and remote employees.
The process to implement this VPN technology has been in existence for some time. The origin of this technology can be found in virtual circuits which was originally produced in late seventies. Virtual circuits are cost effective and easy to integrate with large networks.
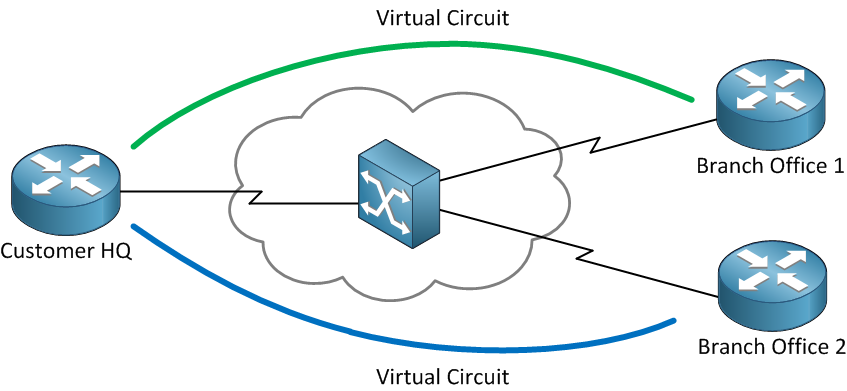
The simple idea behind this virtual circuit is to build a logical path towards destination port from the source port. Many hops are believed to be incorporated between routers to build the circuit, but still the final product acts just like a direct connection between the ports. This method can then be used to communicate between two applications over a shared network. The addition of the encryption equipment to this circuit took this technology to a whole different level and made the connection highly secured preventing attackers from accessing the transmitted information over the network.
The technology behind the functioning of this virtual private network is interesting but at the same time very complicated. The data is transmitted by means of tunnelling. Prior to the transmission of a packet, it is modified with a new header and encapsulated inside another new packet. The routing information linked inside the header helps to traverse a shared network before the packets reach a tunnel endpoint. This logical path which these packets travel through is defined as a tunnel. These encapsulated packets are decapsulated only after reaching the tunnel end points and then forwarded to its target destination. This whole process functions only when the endpoints support a common tunnelling protocol which is operated in the data link or in the network layer. The commonly used protocols are IPsec and SSL. When building a VPN solution, dedicated hardware equipment’s must be put in place to perform the tasks of tunnelling, encrypting and for user authentication. These devices are often placed between the routers and operates as encrypting bridges. Devices like VPN concentrators support remote access tunnelling and is crucial in maintaining multiple tunnels simultaneously supporting large number of users. Meanwhile, consistent logging and reporting options can only be maintained by effective hardware solutions.

Figure 3 : Shoretel VPN Concentrator
Moreover, there a many types of VPN client software that can be installed on PC’s or smartphones for users to establish a private secure network. Installing a dedicated VPN software on servers allows to build a VPN gateway for an entire site and help manage the tunnels over the security gateways. These software-based VPN solutions suits best for remote access connections and provides great flexibility in terms of execution and usage.
